The internet is the lifeblood of the 21st century. There is little that doesn’t happen in the ways of the vast cyberspace. But the convenience harbors grave dangers to personal, social, and various kinds of threats that are hard to detect.
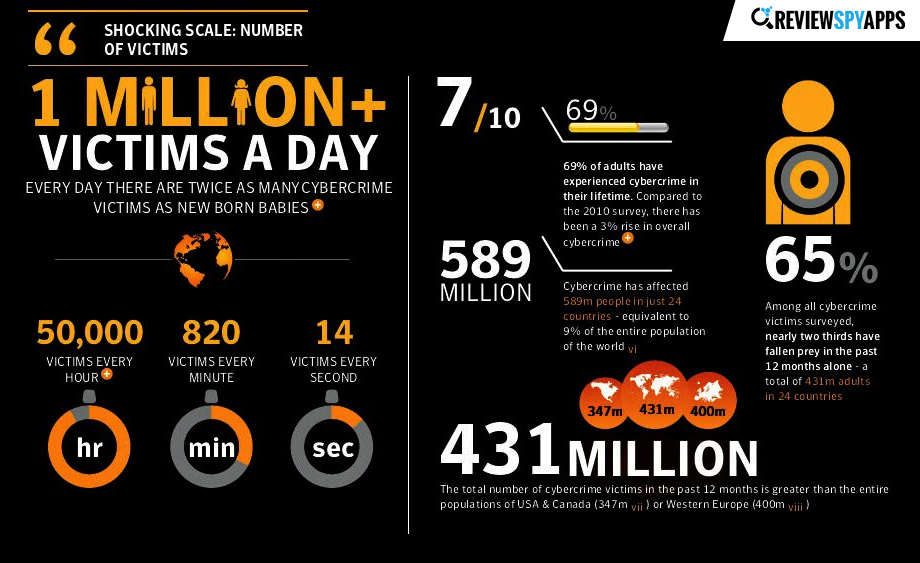
Cyber-security breaches and cyber-crimes are terms enough to terrify anyone nowadays. A report from Cyber-security breaches survey 2018, 43% of businesses reported becoming a victim of a cyber-security breach in the last year.
The internet provides so much to our lives. Our lives are now convenient, unlike any generation before us. But these webs of convenience hide the dark side of the internet from many people. It has gotten so bad that hackers can shut down significant parts of countries with a targeted attack.
The extent of these cyber crimes is far-ranging.
Below are the different categories to explain to you the extent of the issue:-
When done well, hacking gets used to identify weaknesses in computer systems or networks to exploit its vulnerability to gain access. But the word has grown infamy due to its widespread misuse to leak confidential data, secrets and spread chaos.
A 2007 University of Maryland study found that, on average, hackers attack every 39 seconds or 2,244 times a day.
Pornography is the act of showing sexual acts. Many times these are consensual performers, but the issue here is of the individuals who get exploited, and private moments are shared for the world to see without their consent.
In 2014, child sexual abuse imagery crossed 1 million from 3,000 in 1998.
The fraudsters create e-mail messages with a forged sender address, and this act is known as e-mail spoofing.
A glaring example is such an e-mail sent to a news agency allegedly from a Swedish company called Fingerprint cards stating that Samsung has offered to purchase the company.
The news spread and the stock exchange rate jumped up by 50% of the Swedish company, and an investigation got launched.
The act of overflowing a mailbox by sending a large amount of mail containing online abuse gets termed as e-mail bombing. E-mail bombing can get used to taking control of your email.
There have been examples of email bombing services getting offered on the dark web. Rates vary from 15$ per 5,000 messages to 30$ for 20,000 messages.
Cyber-security breaches are like the real Trojan horse; the malicious online Trojan horse misleads the recipient of the actual intent it hides within its walls. The Trojan horse of the story that inspired the term had taken down the city of Troy in the war.
Nowadays, they mostly serve as back door entry into a computer or system.
A 2010 study showed that 70% of computer systems were affected by Trojan horses.
A piece of malicious code that intentionally gets inserted into a software system to act any hostile intentions. These are used as ransom to target specific files to be deleted or corrupted.
In 2002, Roger Duronio of UBS PaineWebber used a logic bomb against his employer on 2000 systems of the company. Two thousand company servers went down and left around 17,000 brokers across the US, unable to make any trade.
When small online attacks lead up to a big strike as the small attacks were left undetected due to their negligible size is what a Salami attack looks like to be. Cyber-security breaches like this are hard to detect.
There have been cases where attackers seized little information as not to attract attention and hence doesn’t even come under illegal.
In 2008, a man got arrested for creating 58,000 accounts with fraudulent methods and used them to collect money through verification deposits from online brokerage firms a few cents at a time.
Web jacking is the act of cloning someone’s website and then tricks the target user or organization into believing that the cloned site is theirs. They place the malicious link on the website, and if you click on it, then the malicious web server replaces it.
Thus, the target will lose all control of their website.
Use of the internet to conduct violent acts that either threaten or result in loss of life and significant bodily harm. Large scale disruption of computer networks is the prime example.
A Nebraska based consortium of small municipal utilities in 2016 detected nearly 4 million hacking attempts in 8 weeks. This attack is just a tiny sample of the dark side of the internet.
Cyber trafficking is another word for human smuggling that gets conducted with the aid of computer networks. It gets covered by 2000 Palermo protocols adopted by the United Nations in 2000 as an example.
According to the FBI, sex trafficking is the second largest growing crime behind drug trafficking.
Illegal copy and delivery of software are one of the most popular illegal businesses in the world. Some varieties of software piracy are:-
– Counterfeiting
– End-user piracy
– Internet piracy
– Hard-disk Loading
– Client-server misuse
BSA Global Software Survey 2018 shows the value of the piracy software globally at 46.3 billion $, with 19 billion $ in North America and Europe only.
The act of wreaking havoc and destroying data instead of stealing or misusing it. It gets achieved through disrupting the digital files or a website, and the purpose here is to make it problematic to use the computer system.
Cyber vandalism is an excellent example of the dark internet web.
The classic Pyramid scheme aims to make money solely by adding new participants. This recruiting is usually done by:
– Promising high return in a shorter amount of time
– No genuine product or service gets sold.
– The emphasis is not on service but on recruiting new participants.
This operation is another side of the digital dark side. This scam gets conducted through an e-mail. The scammer asks for a commission to transfer some money and then disappears with the money.
Some common ways of eliciting people to cheat them:-
– They won a lottery worth millions of dollars.
– They need help to transfer illegal money from an African country.
– Goods getting offered at meager prices.
– They got selected for an overseas job overseas.
A computer virus gets designed to spread from host to host and spreads its web with the ability to replicate itself. It needs a file or document to spread the virus.
Small businesses are at significant risk.
In 2018, a company paid over 930,000$ as a ransom amount.
The world of the world wide web is running this world. Every activity has become much easier to accomplish, and so much time and money get saved as a result. It is effortless to forget in all the wonder of the online word it provides and ignores the dark side of the internet. It is crucial to get quality mobile tracking software to keep oneself and loved ones safe from these online dangers.